
Templates Community /
Network diagram for DDOS
Network diagram for DDOS
Qasim Khan
Published on 2025-10-27

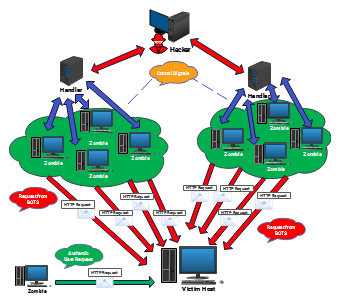
This network diagram visualizes how a Distributed Denial of Service (DDoS) attack is executed. A hacker controls multiple handlers that command networks of infected computers, known as zombies or bots. These bots send massive HTTP requests simultaneously to overwhelm a victim host, disrupting normal service. Authentic user requests struggle to get through due to server overload. The diagram highlights how botnets, command-and-control servers, and malicious traffic interact during an attack. It effectively portrays the structure, flow, and impact of DDoS attacks, helping cybersecurity professionals understand network vulnerabilities and develop stronger defense mechanisms against cyber threats.
Tag
business
IT
network diagram
Denial of Service
DDOS
Share
Report
0
55

Post

 Desktop
Desktop